Microsoft 365 Log Management (1): Getting Started with Sentinel
▶ Watch on YouTube: Microsoft 365 Log Management (1): Getting Started with Sentinel
Why Log Management Matters in Microsoft 365
One of the biggest challenges I faced while managing Microsoft 365 was log management.
Initially, message trace and audit logs were enough. But as I started incorporating security solutions like Microsoft Defender, the amount of data skyrocketed.
How We Used to Do It
Previously, I relied on PowerShell scripts to extract logs, store them in a separate repository, and later manage them via SQL Server for analysis.
While this worked, it had several drawbacks:
- Required a dedicated VM for log collection
- Credential management was cumbersome and posed security risks
- Didn’t align well with the SaaS-first approach
- Frequent schema changes and new log types increased maintenance overhead
In short, the process became increasingly labor-intensive.
Why I Chose Microsoft Sentinel
To solve these issues, I turned to Microsoft Sentinel.
Although Sentinel is primarily a SIEM solution, my initial goal is centralized log management. Here’s why Sentinel stood out:
- Native integration with Microsoft 365
- Automated log collection and schema updates
- Easy integration with Defender, Entra, Intune, and more
The Role of AI
Thanks to AI, the barrier to entry for these technologies has dropped significantly.
With Copilot, I can leverage the data stored in Sentinel more intelligently.
Once logs are ingested into Sentinel, it’s like having a database ready for advanced analytics—and AI can answer questions based on that data.
This marks the beginning of a shift from manual log management to a more automated and intelligent approach.
What is Microsoft Sentinel?
Microsoft Sentinel is a cloud-native SIEM (Security Information and Event Management) solution that collects and analyzes security logs and events from multiple sources.
It supports threat detection, automated response, and security operations efficiency.
Learn more: What is Microsoft Sentinel? | Microsoft Learn
Microsoft 365 Log Collection Architecture
Here’s the architecture I’m planning for Microsoft 365 → Sentinel:
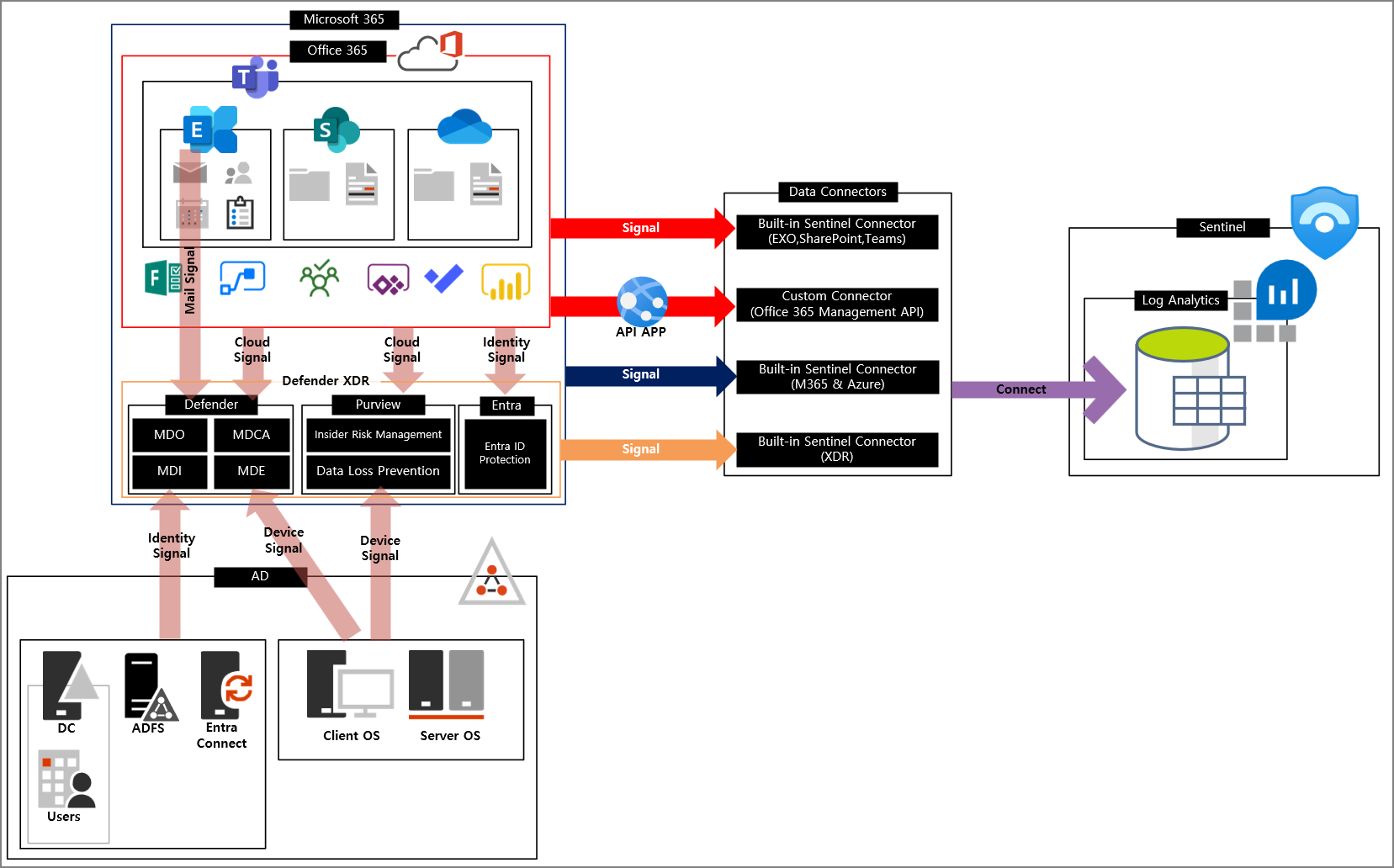
- Signals from various Microsoft 365 services are sent to Sentinel via built-in connectors
- However, not all logs are supported by default
- Unsupported logs require API calls or custom connectors
Note: In this post, we’ll focus on enabling Sentinel. Detailed configurations for each service will be covered in future posts.
Steps to Enable Microsoft Sentinel
1. Access Azure Portal
https://portal.azure.com → Search for Sentinel

2. Create a Sentinel Resource
- Create a new resource group

- Create a Log Analytics Workspace

It is just Log Analytics workspace.
Move to Sentinel → Create

- Add Microsoft Sentinel to the workspace

Adding Microsoft Sentinel

3. Add Microsoft 365 Data Connectors
- Go to Content Hub

Currently, Sentinel is being integrated with the Defender page.
If you go to Defender (Security.microsoft.com) and click on Microsoft Sentinel, you can confirm that it is being provisioned.

If you refresh in the Content hub within Sentinel on Azure, you will see the available Content that can be added as shown below.

For a simple connection test, search for Microsoft Entra ID and proceed with the installation.
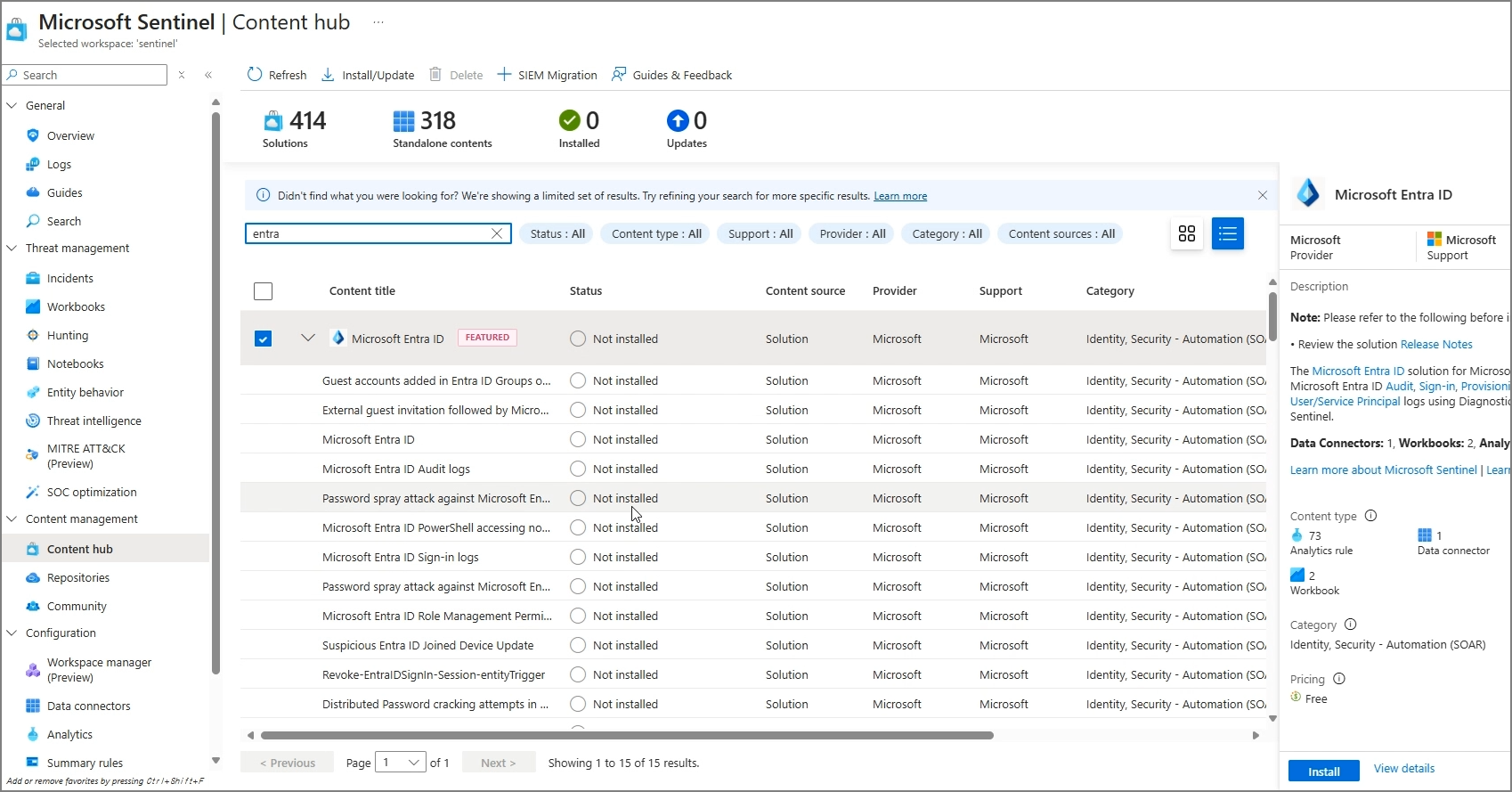
Data Connectors → Microsoft Entra ID → Open connector page
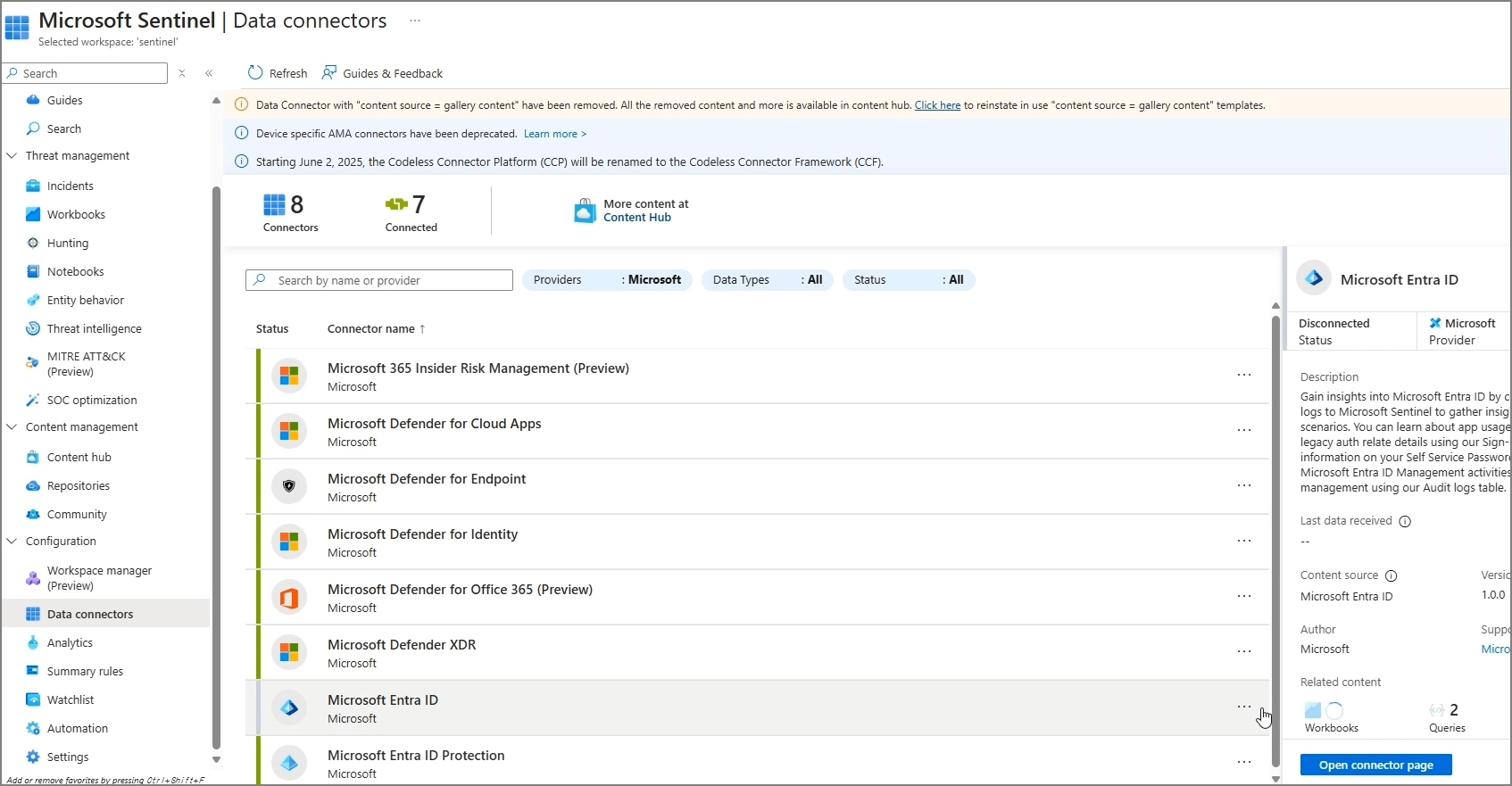
Select the logs to import and apply changes.

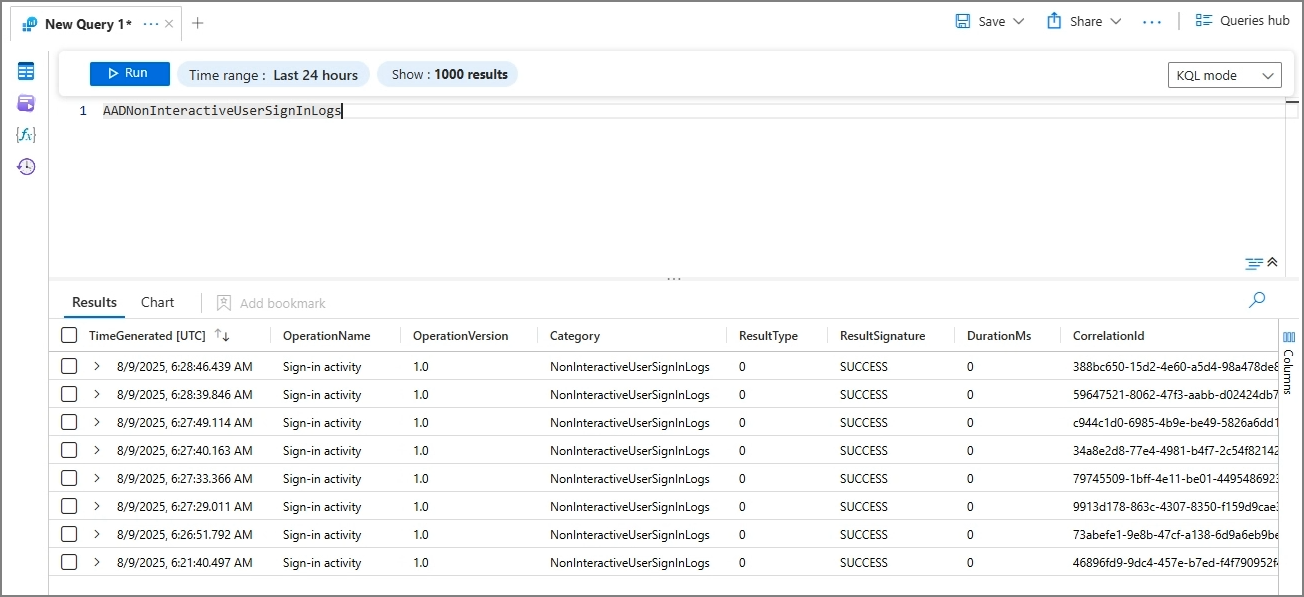
4. Verify Log Collection
- Wait for logs to populate

- Use KQL mode to query and validate data ingestion
What’s Next?
In the next post, I’ll cover enabling specific Microsoft 365 logs and, if needed, the E5 onboarding process.
Tip: If you’re planning to integrate Sentinel with Microsoft 365, start small—enable core connectors first, then expand gradually.