I will discuss Tenant restriction settings.
The primary purpose of Conditional Access is to prevent company accounts from being accessed on personal devices. However, Conditional Access cannot prevent other company accounts from being accessed on company devices.
Of course, if a company device can access Naver Mail and Google Drive, it means the company is not very concerned about data leakage, and you may disregard this post.
To use M365, you need to open MS-related URLs such as office.com. Tenant Restriction is a concept used to prevent access with other company or personal accounts (such as outlook.com) during this time.
Youtube (English)
Technical article
Configure tenant restrictions - Microsoft Entra ID - Microsoft Entra External ID | Microsoft Learn

There are three main methods:
- GSA
- Company Proxy Equipment
- GPO
The method using GSA requires a prior understanding of GSA.
I will cover that part separately later.
In this post, I will apply tenant restrictions using the third option, GPO.
Step 1: Configure default tenant restrictions v2
Entra Admin Center > Cross-tenant access settings > cross-tenant access settings > Default settings

Edit tenant restrictions defaults
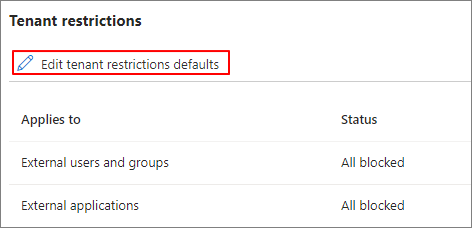
Create Policy
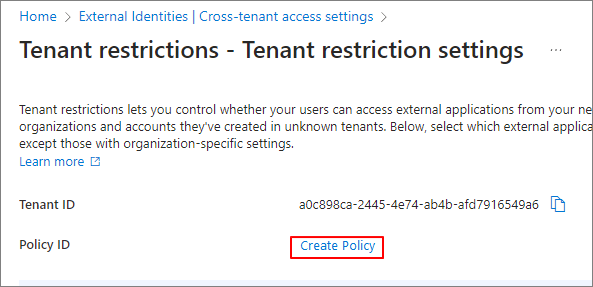
The Policy ID is generated as shown below. Make sure to copy each value and keep them.
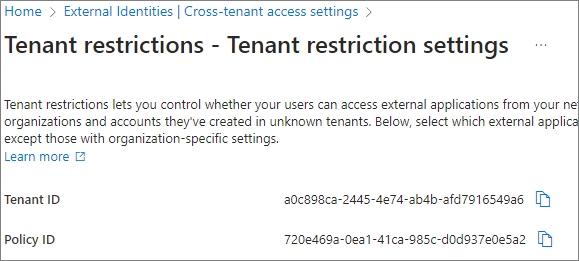
To set up a blocking policy for external accounts, configure it as shown below (default settings).

To block all external apps, configure the settings as shown below.

Step 2: Enable tenant restrictions on Windows managed devices (preview)
In the technical documentation, there are guidelines as shown below.
Tenant restrictions V2 on Windows is a partial solution that protects the authentication and data planes for some scenarios. It works on managed Windows devices and does not protect .NET stack, Chrome, or Firefox. The Windows solution provides a temporary solution until general availability of Universal tenant restrictions in Microsoft Entra Global Secure Access (preview).
-> Although the content is difficult to understand, it can be interpreted as indicating that the feature will be provided in a different way in the future. Currently, it is in the preview stage.
Download the ADMX files for the latest Windows GPO policies.
Once installed, the policy files will be saved to the following location.

Depending on the method of policy deployment in AD, copy the PolicyDefinitions folder to the appropriate location with only the necessary languages. (This part of the policy is related to AD, so we will not cover it here.)
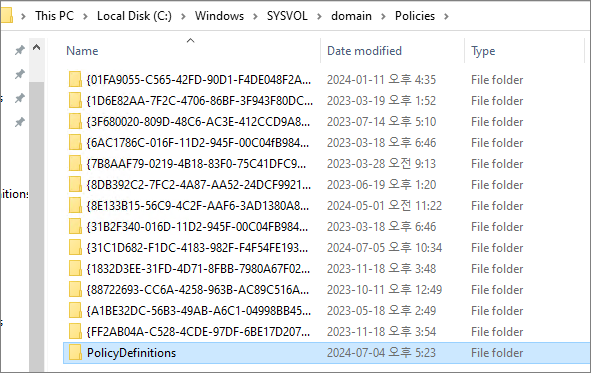
Run gpmc.msc on the Domain Controller (DC).

Create a policy in the Organizational Unit (OU) that you will use for testing. Right-click and select "Edit".
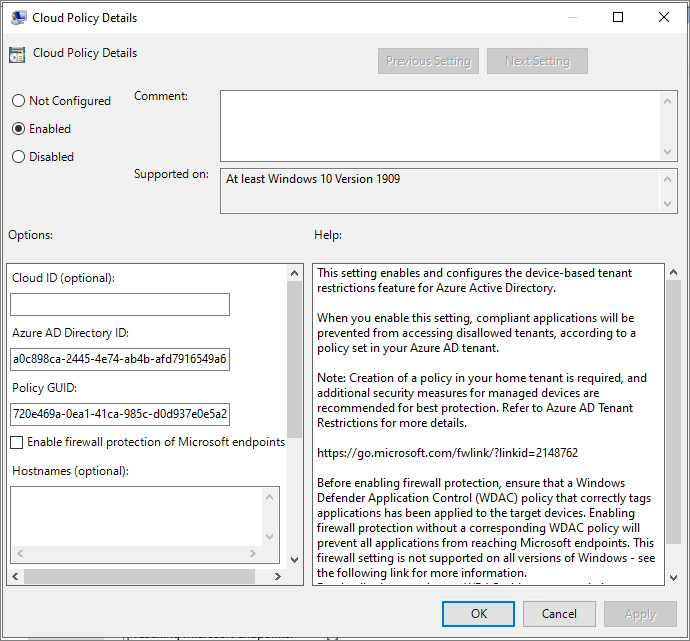
Computer Configuration > Administrative Templates > Windows Components > Tenant Restrictions

Configure the settings as shown below.
Attempt to log in with a personal account on Edge.

Verify that access is blocked as shown below.

You can also see that access is blocked when attempting to log in with another tenant account.

'Microsoft 365 > Entra' 카테고리의 다른 글
| Entra. Verified ID (2). Enable & Test (English) (1) | 2024.09.20 |
|---|---|
| Entra. Verified ID (1). Introduction (English) (0) | 2024.09.20 |
| Microsoft Entra ID. Set up tenant restrictions v2 by GSA (English) (0) | 2024.07.07 |